Real-time SBOMs
Accurate CycloneDX and SPDX from your CI. Direct and transitive dependencies tracked continuously.
Accurate CycloneDX and SPDX from your CI. Direct and transitive dependencies tracked continuously.
Move beyond CVE dumps. Prioritize what is actually exploitable and fix with full context.
Track APIs, SDKs, SLA expiry and breach history alongside your code dependencies.

Critical, High, Medium and Low exposure in one place. Watch risk change as your code evolves.
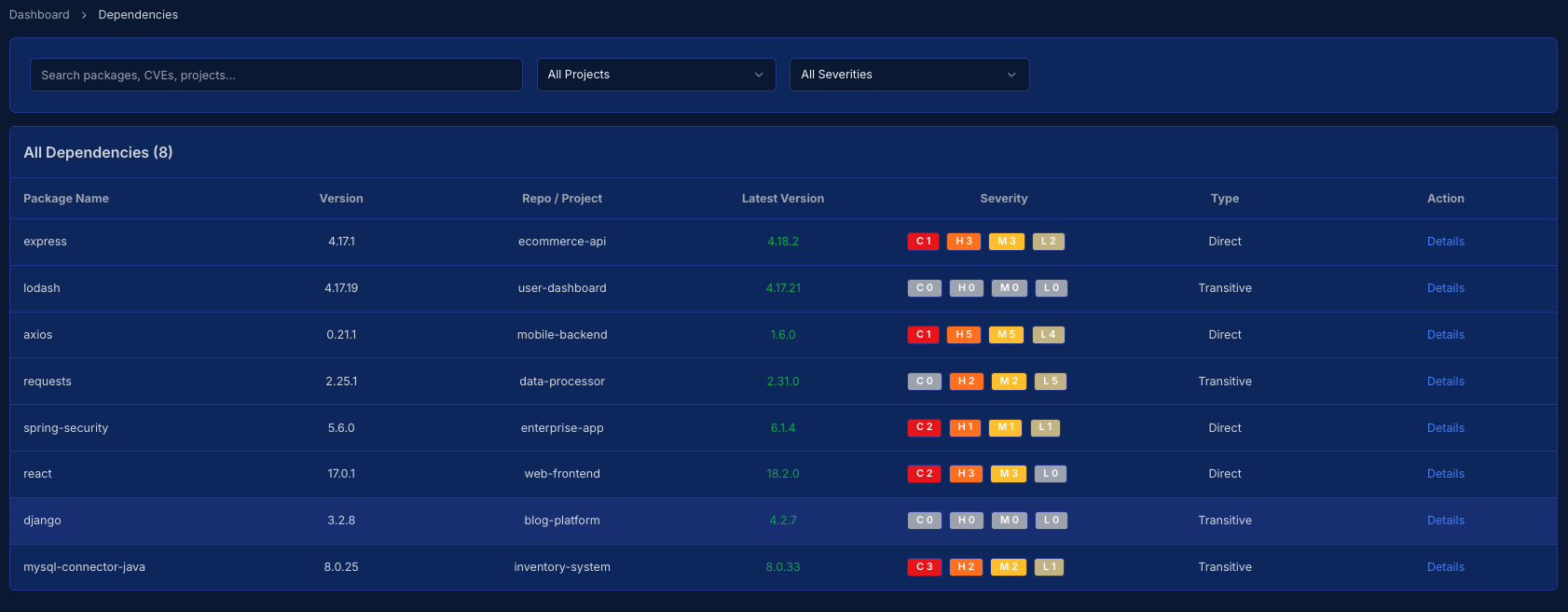
Every package, every CVE and every version in one view. No black box. Built for developers.
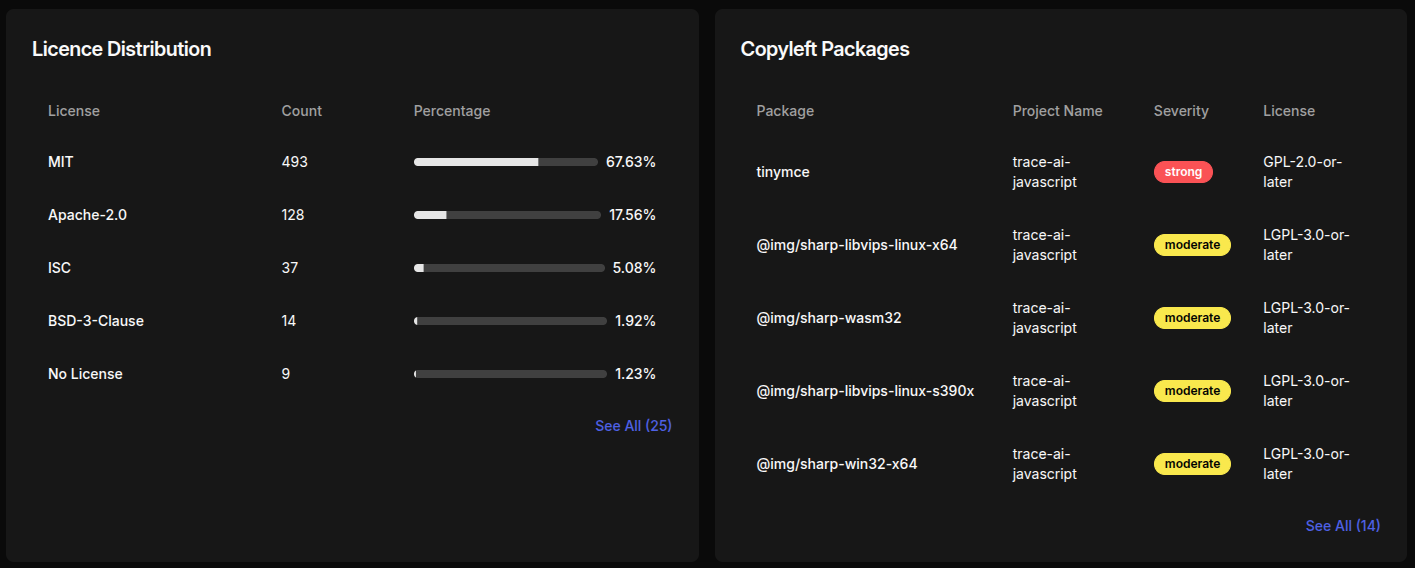
Identify GPL, LGPL and other copyleft licenses instantly. Avoid surprises during enterprise review.
Connect your repository and watch as Trace-AI automatically generates comprehensive SBOMs, scans for vulnerabilities, and validates license compliance.
Link GitHub or GitLab repository
Analyze dependencies and generate SBOM
Track vulnerabilities and compliance
Generate audit-ready reports
We publish everything. Trace-AI is not a black box. ZSBOM is open and auditable.
GitHub or GitLab. Minimal setup.
Direct and transitive dependencies.
Exploit context. Not just CVE lists.
In one dashboard.
CycloneDX, SPDX and JSON.
What is in your product maps cleanly to your audit checklist. No spreadsheets.
First 5 repositories free. Predictable per-repo pricing as you scale.
Be first to try new features and early adopter perks.
A Software Bill of Materials (SBOM) is a complete inventory of all components in your software. It's essential for understanding your security posture, managing vulnerabilities, and meeting compliance requirements. With increasing regulatory pressure and supply-chain attacks, having an accurate, up-to-date SBOM is critical.
Traditional scanners report all CVEs, creating noise and alert fatigue. Exploit-aware scanning prioritizes vulnerabilities that have known exploits in the wild, helping you focus on real risks first. We integrate multiple threat intelligence sources to determine exploitability.
Trace-AI supports all major ecosystems including npm/yarn (JavaScript), pip (Python), Maven/Gradle (Java), Go modules, RubyGems, NuGet (.NET), Cargo (Rust), and more. We continuously add support for new package managers and languages.
Yes. We only analyze dependency manifests and lock files – never your source code. All data is encrypted in transit and at rest. We only access your dependencies file and our workflow is metadata driven. You can also run ZSBOM locally for complete control.
ZSBOM is fully open-source and transparent. Unlike black-box commercial tools, you can audit our classification logic, customize risk scoring, and contribute improvements. We focus on accuracy, exploit-awareness, and developer experience.
We map SBOM data to ISO 27001, SOC 2, PCI-DSS, HIPAA, and GDPR requirements. Our policy-as-code library includes pre-built compliance checks that you can fork and customize for your specific needs.